Counter-Terrorism Security Risk Assessment
Thursday, 20th October 2022
Following a competitive tender process, Trident Manor was selected to undertake a Counter-Terrorism security risk assessment of a high-profile cultural and hospitality venue in Manchester.
Trident Manor was selected from multiple other consultancies, some with a global presence, to undertake a security risk assessment of a high-profile venue within Manchester city centre to evaluate current vulnerabilities, the level of preparedness that exists, and provide recommendations to address and better protect visitors, staff and the building from the impact of a terrorist attack.
Prior to submitting the proposal, the request for a site visit was accepted so that discussions with the in-house team could take place in order to understand the outcomes they wanted/expected and to allow an initial understanding of the organisation’s approach to risk management and their risk tolerance/acceptance levels. This is extremely important because if they only wanted a tick-box solution to a complex issue then our time and effort would have been wasted and we would not have submitted a proposal.
As it happens the initial meeting was a great success for all parties as it allowed them to ask questions about our understanding of operating within a cultural setting and me to establish that they wanted to be proactive in their protection of assets (including visitors) from acts of terrorism. The time was also spent being shown around the site so that a more detailed understanding of what was needed could be contextualised and levels of vulnerabilities start to be understood.
The visit highlighted to us that there was a genuine desire to meet ‘duty of care’ obligations but also from the client’s perspective that Trident Manor was indeed a specialist consultancy who were able to meet their needs.
Irrespective of the organisation, or reasons for undertaking a security audit or assessment we will always follow a set process so that clients can understand what we are doing and what stage has been reached. Our process consists of five stages which we always follow:
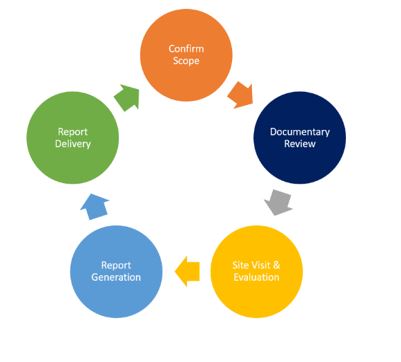
Each stage is as important as the other in ensuring highly-professional and cost-effective services are provided. If somebody is opening their hearts to us and telling us about their concerns, weaknesses, and vulnerabilities the first thing that we do during stage 1 (Confirm Scope) is to sign a non-disclosure agreement to demonstrate that we are serious about protecting any information that is shared or uncovered during the assessment.
The next stage is to review any related documentation that the client may, or may not have. This is normally done at our office so that time can be taken to absorb the information allowing procedures and operational practices to be evaluated during the site visit, and it is cheaper and more cost-effective for the client.
The site visit and evaluation stage is critical as it allows different terrorist attack methodologies to be considered and their impact assessed. It also allows rational thought processes and recommendations to be made that are risk-based and client specific.
During this evaluation, the blast impact of VBIED (car bombs), PBIED (suicide vests), and place devices were all considered. As there was a lot of glass throughout the building the impact of glass fragmentation could have resulted in multiple casualties, even death depending on where the device was initiated and its size. We considered the threat and impact posed by an MTA (marauding terrorist attack), the use of a vehicle as a weapon, and bladed weapon attacks.
We evaluated the existing physical measures and how they would be impacted by any of the terror attack methods, whether they could withstand the impact or whether there were sensible and realistic measures that could be adopted to increase the resilience and robustness to reduce the risk and protect people.
We also looked at the operational practices to understand levels of vigilance and awareness and whether procedures existed that help reduce and manage the risks that exist or can be anticipated. Finally, we evaluated whether there was any training needed to improve the likelihood of pre-attack hostile surveillance being detected and whether staff knew what to do in the unlikely event that a terrorist attack occurred.
This assessment was conducted during the day and at night by declared and undeclared staff, some of whom undertook a successful penetration test where access was gained to sensitive areas.

Following the assessment, a full report outlining the findings, vulnerabilities, effective practices, and risk reduction recommendations was prepared. Often consultancies do not clearly articulate their methodology and risk assessment processes, so the client does not always know how decisions or recommendations have been reached. We always outline our risk-assessing process and clearly articulate what risks exist and the proposed risk-reduction strategies that are sensible, pragmatic, and achievable.
When making recommendations it is not the role of a security consultant to protect all assets at all costs; ultimately it won’t work because it is an unachievable goal. The recommendations have to be proportionate because if the client is unable to operate then the protective recommendations become counter-productive and can hasten the demise of the client. Another consideration is the cost-benefit of the recommendations being made against the risk of it occurring. The consultant may advise that blast-resistant materials be applied to a building costing £2 million if the client then chooses to ignore the recommendation because it cannot afford to implement it has the consultant done their job? They may think so, but have they acted in the best interests of the client or protected themselves if things go wrong?
Wherever possible our reports try to explain the reasoning behind recommendations and offer multiple solutions for the client to consider. We view the purpose of any report that we generate as being a tool to enable informed decisions to be made by the client through the sharing of open and honest advice and guidance.
The final stage of the assessment process is the report delivery. When dealing with international clients or clients away from home it is sometimes difficult to deliver it in person. Sharing electronically has become a standard practice but we always encrypt our reports and try to send the passwords by secondary electronic means (text, teams, WhatsApp etc.).
After sharing the report we believe that it is appropriate to always offer to deliver a presentation so that questions can be asked, and issues clarified. This can again be done in person or electronically.
By following this process we know that we have continually considered the client’s needs and requirements.
In this project, several observations were made to reduce the risks faced by introducing some physical security modifications, reviewing and updating governance, and developing a proactive training programme that was suitable for all. (You didn’t think we were going to go into detail did you?)
Organisations and businesses may have legitimate concerns about whom they turn to for advice and guidance. The first thing that we would say is that the government is attempting to address this by identifying what and who can be viewed as a ‘Competent Person’. This is very difficult as what do they base it on?
Our managing director has counter-terrorism experience going back to the 1980s and more recently within a diplomatic security role operating in places as diverse as Colombia, Saudi Arabia and Pakistan where the threat from terrorists was a risk that required daily management. He has undertaken threat, risk, and vulnerability assessments including from terrorist threats for corporate and critical infrastructure clients all over the world. He has a Master of Science degree in security and is a chartered security professional. However, he has not done a police terrorist training course and therefore is he competent despite 40 years of experience at strategic and operational levels.
Equally, a member of the Counter-Terrorist Police (CTP) could have no experience, was in an administrative role before joining the CPT but has done a police course that nobody else can access, as was said this is a very difficult question that will hopefully be answered within the next 12 months. This will hopefully be resolved in the coming months, and everything will be clearer for all.
In the meantime, check to see if you qualify for the free services being provided by the CTP whether that is training or more formal assessments. There are some brilliant online resources available for everybody via CTP, CPNI, or the Protect App.
Commercially organisations can do due diligence on potential suppliers, anybody who says they can make you ‘Protect’ compliant is either a liar or can see into the future. The legislation has not been finalised so don’t believe the hype they may give you.
Research the organisation/individual offering services, interview them and get a feel for whether they are a good fit for your organisation, you are the client not them. Establish whether they have worked with your type of organisation and ask for references, preferably from somebody within your sector.
Just because they are ex-military or police it doesn’t mean they understand security or the specific threat posed by terrorism, equally, just because an organisation is a global brand it doesn’t mean that they have the necessary in-house expertise and as the saying goes good things can come in small packages.
Trident Manor does have the necessary experience and expertise to support you and help manage the risks that you face, from whatever sources and wherever in the world. Our specialist training services are designed to meet the requirements of individual clients and cover a wide range of counter-terrorism programmes not offered elsewhere.
We are always contactable and ready to support you in managing the threats that you face. Contact Us
